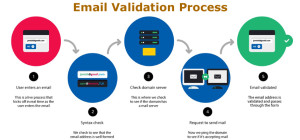
Securing dental software on the cloud is of paramount importance to protect sensitive patient data, maintain regulatory compliance, and prevent unauthorized access. Cloud-based solutions offer numerous benefits like scalability, accessibility, and cost-efficiency but also introduce potential security risks. Implementing a robust security strategy is crucial to safeguard your dental software and the data it holds. Here are essential steps to secure your dental software on the cloud:
1. Choose a Reliable Cloud Service Provider:
Selecting a reputable cloud service provider is the foundation of your security strategy. When searching for healthcare providers, it is important to consider their history of success in the industry and whether they comply with standards such as HIPAA. It is also crucial to assess their security certifications, approach to data encryption, and ability to recover from disasters before choosing a provider.
2. Encryption and Data Protection:
Ensure all data transmitted to and stored in the cloud is encrypted using strong encryption algorithms. To ensure unauthorized individuals cannot access data during processing, while in transit, or at rest, it’s essential to protect it with encryption. To limit access to sensitive information, implement role-based access control (RBAC) and regularly review user permissions to prevent unnecessary exposure.
3. Multi-Factor Authentication (MFA):
Require multi-factor authentication for all user accounts accessing the dental software on the cloud. Multi-factor authentication (MFA) enhances security by verifying the user’s identity through a range of methods, including passwords, biometrics, or one-time codes sent to a trusted device.
4. Regular Backups and Disaster Recovery:
Make sure to frequently back up your dental software data and configurations to a secure location. In the event of data loss or a security breach, having up-to-date backups ensures minimal disruption and reduces data loss. Test the disaster recovery process periodically to confirm its effectiveness.
5. Implement Network Security Measures:
Employ firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs) to safeguard the network infrastructure. Implementing these security measures is crucial in preventing unauthorized access and safeguarding data while it is being transferred between users and the cloud server.
6. Regular Security Audits and Penetration Testing:
Conduct periodic security audits and penetration tests to identify vulnerabilities and weaknesses in your dental software and cloud infrastructure. Address any issues promptly to maintain a secure environment.
7. Keep Software and Systems Updated:
Ensure your dental software, operating systems, and cloud infrastructure components are regularly updated with the latest security patches and fixes. Outdated software can be more susceptible to cyber threats.
8. Train and Educate Staff:
One of the main reasons for security breaches is human error, which highlights the importance of providing comprehensive training to all employees who have access to dental software on the cloud. This training should cover best practices, proper data handling procedures, and how to identify and report possible security threats.
9. Secure APIs and Integrations:
If your dental software interacts with other systems or third-party applications, secure the APIs and integration points to prevent unauthorized access or data leakage.
10. Compliance and Regulations:
Adhere to industry-specific regulations like HIPAA and any other data protection laws relevant to your location. Compliance with these standards helps ensure the security and privacy of patient data.
11. Monitor and Analyze System Activity:
Implement real-time monitoring and logging of system activity to detect and respond quickly to suspicious behaviour. To effectively centralize and analyze log data, it is recommended to make use of security information and event management (SIEM) tools.
12. Incident Response Plan:
It is important to create a detailed plan for responding to security breaches or data compromises. This plan should include specific steps to be taken and should be regularly reviewed and updated to address new threats and security trends.
Conclusion
By following these best practices, you can enhance the security of your dental software on the cloud, protect patient data, and instill confidence in your practice’s ability to handle sensitive information responsibly. Remember that security is an ongoing process, and staying vigilant is crucial to keep pace with evolving cyber threats.