DITSCAP (Department of Defense Information Technology Security Certification and Accreditation Process) and NIACAP (National Information Assurance Certification and Accreditation Process) are two frameworks used by the United States Department of Defense for the certification and accreditation of information systems.
DITSCAP (Department of Defense Information Technology Security Certification and Accreditation Process) and NIACAP (National Information Assurance Certification and Accreditation Process) are two frameworks used by the United States Department of Defense for the certification and accreditation of information systems.
Both DITSCAP and NIACAP aim to ensure the security of information systems by assessing the system’s security risks and vulnerabilities, and ensuring that appropriate security measures are in place to mitigate those risks. However, there are some differences between these two frameworks.
DITSCAP was the first framework introduced by the Department of Defense, and it was used for the accreditation of information systems until 2006 when it was replaced by NIACAP. DITSCAP had six phases, which included definition, verification, validation, post-accreditation, and re-accreditation. The framework was designed to provide a structured approach to the certification and accreditation of information systems, and it required a significant amount of documentation.
NIACAP, on the other hand, was introduced in 2000 as a replacement for DITSCAP. The framework was designed to be more flexible and streamlined than its predecessor, and it had four phases: initiation, certification, accreditation, and maintenance. NIACAP was designed to be less prescriptive than DITSCAP, and it allowed for more flexibility in the certification and accreditation process.
One of the major differences between DITSCAP and NIACAP is in their approach to risk management. DITSCAP focused on the identification and assessment of risks, while NIACAP focused on the management and mitigation of risks. NIACAP placed a greater emphasis on the ongoing monitoring and evaluation of security controls, and it required that risk management be an integral part of the system’s life cycle.
Another difference between DITSCAP and NIACAP is in their approach to documentation. DITSCAP required a significant amount of documentation, including a system security plan, a security assessment report, and a security accreditation package. NIACAP, on the other hand, was designed to be more streamlined and flexible, and it allowed for the use of alternative documentation formats.
Despite these differences, both DITSCAP and NIACAP share the same goal of ensuring the security of information systems. They both require the identification and assessment of security risks, the implementation of appropriate security controls, and the ongoing monitoring and evaluation of those controls. They both also require the involvement of multiple stakeholders, including system owners, users, and security professionals.
In conclusion, DITSCAP and NIACAP are two frameworks used by the Department of Defense for the certification and accreditation of information systems. While there are some differences between these two frameworks, they both share the same goal of ensuring the security of information systems. DITSCAP was the first framework introduced by the Department of Defense, and it was replaced by NIACAP in 2006. NIACAP was designed to be more flexible and streamlined than its predecessor, and it placed a greater emphasis on risk management and ongoing monitoring and evaluation of security controls.
Both DITSCAP and NIACAP have a series of phases that must be completed in order to achieve certification and accreditation of an information system.
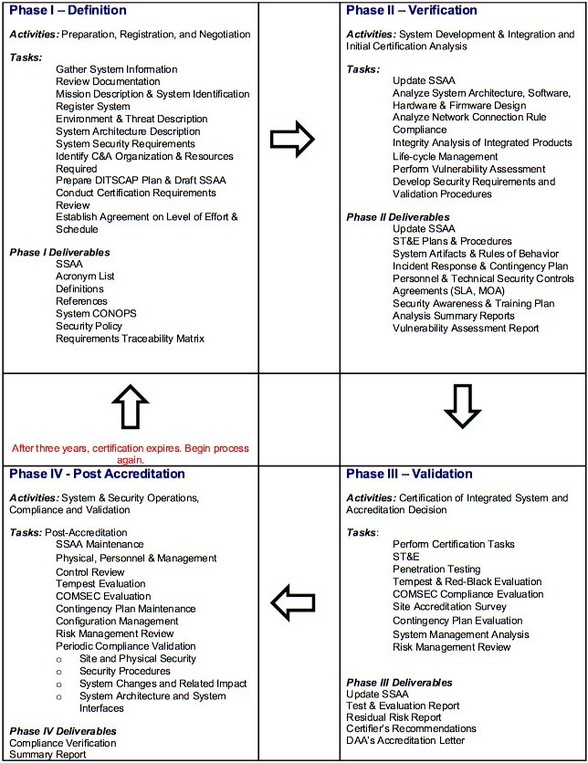
DITSCAP has 4 main phases and 2 optional.
1. Definition: This phase involved defining the security requirements of the system and identifying the security controls that were needed to meet those requirements.
2. Verification: This phase involved verifying that the security controls were implemented correctly and that they were effective in mitigating the identified risks.
3. Validation: This phase involved validating that the system met the security requirements and that the security controls were operating effectively.
4. Post-Accreditation: This phase involved ongoing monitoring of the system’s security to ensure that it continued to meet the security requirements.
5. Re-Accreditation: This phase involved periodic re-evaluation of the system’s security to ensure that it continued to meet the security requirements.
6. Decommission: This phase involved the decommissioning of the system when it was no longer needed.
NIACAP PHASES
NIACAP, on the other hand, has four phases:
1. Initiation: This phase involved identifying the system to be certified and accredited, and establishing the certification and accreditation team and their roles and responsibilities.
2. Certification: This phase involved conducting a risk assessment of the system, developing a security plan, and implementing security controls.
3. Accreditation: This phase involved reviewing the security plan, assessing the effectiveness of the security controls, and determining whether the system met the security requirements.
4. Maintenance: This phase involved ongoing monitoring and evaluation of the system’s security controls to ensure that they continued to be effective in mitigating risks.
Overall, the phases of DITSCAP and NIACAP are similar in many ways, but NIACAP’s emphasis on risk management and ongoing monitoring and evaluation sets it apart from DITSCAP. Both frameworks aim to ensure the security of information systems by assessing risks and implementing appropriate security controls, and both require the involvement of multiple stakeholders throughout the certification and accreditation process.