The internet is widely used by millions of people from all around the globe on a daily basis. The use of the internet rises many questions about privacy and security of the users. It is considered that data on the internet is less and less safe every day. Many people use specialized security software called a firewall in order to protect their computers by blocking unwanted content and malicious software.
Another popular way to protect your privacy while browsing the web is by using a virtual private network, also known as VPN. Virtual private network enables users to connect their computer to a virtual network that encrypts the data they send and receive. VPNs do not keep track of web sites their users visit, which means that users can browse the internet anonymously. Basically, a VPN’s function is to protect the communication between two distant users, which communicate over a public network, i.e. the internet. The users communicate like they are in a local network, although their interaction travels across a public network.
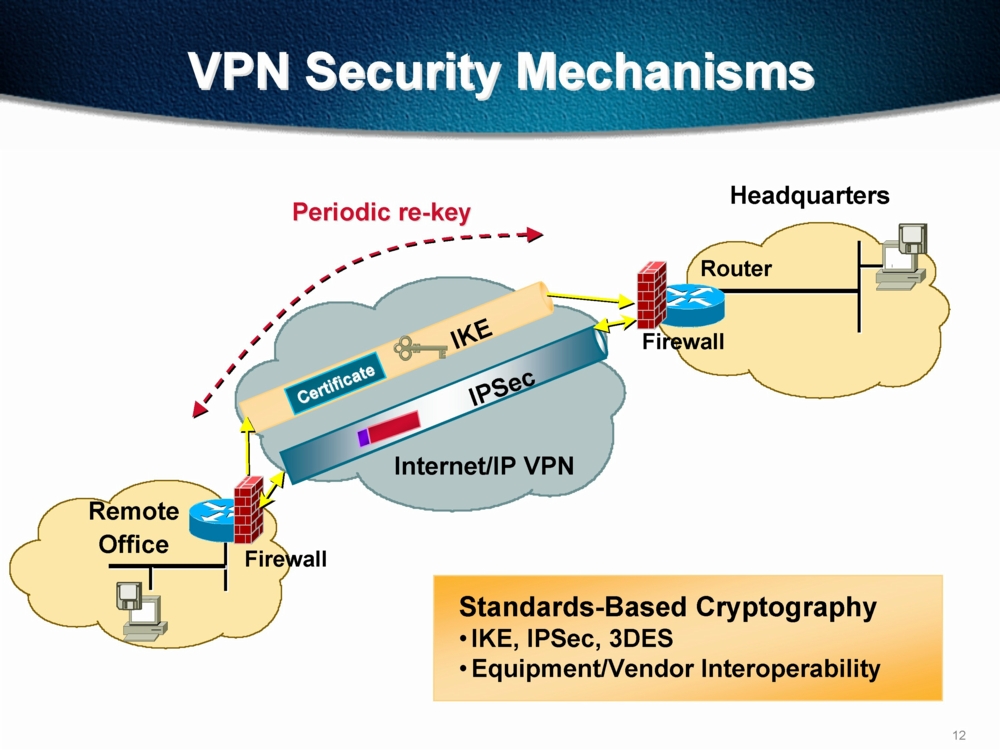
Tunneling is one of the most important components of the virtual private networks. During the process of tunneling, routers on a public network transport packets belonging to a private network. Since the routers recognize VPN packets as any other packets, they treat them like everyday traffic.
Encapsulation is a process that adds additional headers to the original packets. These headers contain information necessary for routing, so that the new packet can be transported freely over the public network. The term tunnel or tunneling is used because the VPN packets can be decrypted and accessed only by the users on the point of origin and destination. These two points are located on private networks and the transfer of data between the them goes through a so called tunnel. When packets reach their destination on another private network, a process known as deencapsulation is performed and data is decrypted and made available to the destination user. The whole process of encapsulation, transport and deencapsulation is called tunneling.
There are many advantages of tunneling and we will mention some of them. Despite the data traveling through an insecure public network, it is encrypted and the access is not allowed to unauthorized users, which makes tunneling a pretty safe way to transport data. Next, it is easy to implement this technology because it is implemented only on the user side and it is not necessary to perform any changes in the already existing infrastructure of public networks. The costs are low when it comes to using virtual private networks. Encapsulation enables transport of data from unroutable protocols.
Virtual private networks are used by many companies in the world. Companies with many different offices and branches in different cities, countries and on different continents use the internet to communicate with their employees. This communication is more secure when it goes over a virtual private network because it is much harder to break the encryption and gain access to protected data.
Besides VPNs created and used by companies and other institutions from all around the world, there are many virtual private networks for internet users looking for anonymity on the internet. Best VPN service reviews and news can be found on a number of websites, some of the VPN’s charge for their use while others are free. Free virtual private networks have certain limitations. We will mention some of the most popular VPNs out there.
TorGuard has different types of servers suited for different activities on the internet. For example, they offer different servers for torrents, anonymity and encryption, etc. They do not store any information about users’ activities whatsoever. Both desktop and mobile operating systems are supported. Different service plans with different prices are offered.
CyberGhost offers their users both free and paid subscriptions. A free account will add certain level of security while paid subscription plans offer increased level of security and anonymity and other options. Although they do not keep tracks of users’ traffic, some information is retained.
Next on the list is Hidemyass. A small Hidemyass review will give you basic details about this popular VPN service founded in 2005 in the United Kingdom.
Hidemyass offers several subscription plans tailored to the needs of a particular user. They offer more than 600 servers in 76 countries, their services can be used on multiple devices at the same time and they are compatible with major operating systems, such as Windows, Mac, Android, iOS and others. Hidemyass logs some information about their users, like some cookie data, etc.
If you decide to start using a VPN, we suggest you do a research and compare different VPN provides across the internet to choose the one that best suits your needs.






![8 Mind Blowing Facts about Fiber Optics [Infographic]](https://lerablog.org/wp-content/plugins/wp-thumbie/timthumb.php?src=http://lerablog.org/wp-content/uploads/2017/02/INFOGRAPHIC-8-Mind-Blowing-Facts-About-Fiber-Optics.jpg&w=300&h=140&zc=1)