VPN is all about securing your data to let you access the world of the internet with complete freedom. It means that when you use a VPN, there is no fear of being intercepted by the government, ISP or any hacker.
A VPN is not something that follows a magic code to give you the power of bypassing strong geo-blocks, there is a whole logic and working behind.
VPN tunnel is a part of the VPN working that keeps your data secure against interceptions. In this blog, you will know what a VPN tunnel is and why you need it.
The Overview
I will possibly try to make you understand the entire phenomenon easily with less technicality. Before hopping into the details, let me tell you that all the VPNs comprise the same working method.
No matter if you’re living in the USA or using an online VPN, the working process will remain the same.
However, you can change and select any location using a VPN. Ultimately, you will appear online from your selected location on your requested server.
It means that if you’re physically living in the USA and selected UK as your server location, then your requested servers will see you as the UK citizen and unblock UK content for you.
Now, let’s dig deeper into the details and explore everything that you need to know about VPN tunneling.
What is VPN tunneling?
There is no tunnel involved physically, of course. When we talk about a VPN tunnel, it refers to the secure connection that allows your data to pass through it, before directly travelling on the requested servers.
At its simplest, a VPN tunnel is an encrypted link that works as a cover between your data and the other network.
The VPN tunneling process compresses your data in the encrypted data packets so on one can access it. Now, I will explain to you why you need VPN tunneling process.
Why do you need VPN Tunneling?
A VPN tunnel is required to protect the users’ connection. It involves two processes. One is for data encapsulation and the other process is for data encryption.
The data encapsulation process covers your data packets inside another data packet for maximum protection.
The data encryption process masks your data with encryption code in such a way that no unauthorized individual can have access or read it.
The encryption process is not necessary to run a VPN tunnel. It means that a VPN tunnel can work without encryption. However, to ensure maximum data security, encrypted connection is needed.
The level of encryption in a VPN tunnel is directly associated with the VPN protocols. Below, I am explaining to you a few most common types of VPN tunneling protocols.
Types of VPN Tunneling Protocols
Here’s a quick look at the most commonly used VPN tunneling protocols:
- PPTP
- L2TP/IPSec
- SSTP
- OpenVPN
All the mentioned VPN protocols are standard protocols used by the industry-leading VPNs.
- Protocol PPTP
PPTP refers to the Point to Point Tunneling Protocol. This protocol is widely used by the VPN services because of its easy to configure ability. PPTP protocol creates a tunnel on your network connection and encrypts your data packets accordingly. Later, the PPTP protocol sends those encrypted data packets through the tunnel.
However, the PPTP protocol is the Fastest protocol, but the provided encryption level is very low, and it only needs username, password and server name to connect to the required server.
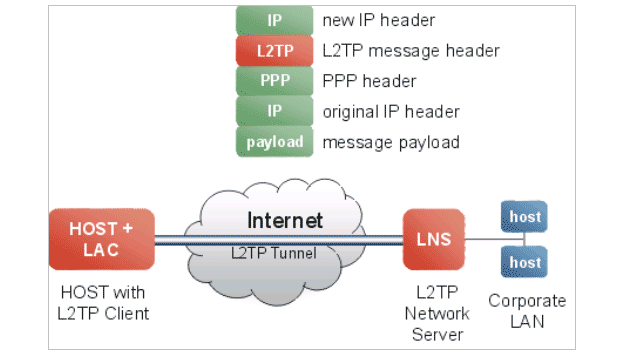
- Protocol L2TP/IPsec
L2TP protocol refers to the Layer 2 tunneling protocol. It’s widely been used in combination with IPsec (internet protocol security). The combination of both protocols offers a much higher level of encryption than the PPTP protocol.
Just like PPTP protocol, L2TP also encapsulates data packets but IP sec provides added security by covering that data with another layer of encryption.
Basically, there are two layers of encryption involved that makes your data even secure and then your data packets travel through the tunnel.
The level of encryption provided by the L2TP/IPsec is the most advanced encryption called AES-256bit encryption. However, due to the double encryption, the L2TP/IPsec process is way slower than the PPTP protocol.
- SSTP
SSTP refers to the Secure Socket Tunneling Protocol. It lets your data travel on the internet through Secure Socket Layers that is also known as SSL.
SSTP particularly works for Windows. It cannot work for every operating system. The SSL helps your data packets to travel through SSTP which is quite secure than L2TP and required no struggle with firewalls because of its unfixed port.
SSL also works in a combination with TLS that is Transport Layer Security. Both protocols function well with your web browsers.
SSL and TLS together add an added layer to your requested site and form an even secure connection for the device that you’re using.
If you want to check the implementation of this combined protocol, then you can see the URL of your requested website. The URL will start from “https” instead of “http”.
- OpenVPN
Just like its name, OpenVPN is an open-source protocol that is used by major operating systems including, iOS, Android, Linux, Mac and Windows.
Since it is an open-source protocol therefore, the code is regularly monitored by the expert security teams.
OpenVPN is not easy to configure and requires third-party involvement for the proper setup.
However, the provided encryption level is strong that AES- 256-bit encryption. It keeps users data secure over the web and also evades the firewalls with faster connection speed.
Wrapping Up
This is all about VPN tunneling and protocols that are used to decide a VPN’s encryption level. I hope that you will find this guide useful and after reading this, you have understood the basics of VPN tunneling and its related protocols.
Contributed by https://fastestvpn.com