
According to a 2016 study by the University of Phoenix, approximately two thirds of all US adults who use popular social media platforms are aware their accounts have been hacked at least once. With 76% of online adults using social media according to statistics by the Pew Research Center, that figure is nothing to sneeze at.
It may be intuitive to keep credit card numbers and your passwords online, but cybercriminals can do a great deal of damage even without those two pieces of data. Besides the basic registration requirements like your name, birth date and contact information, the details of your personal life, including where you live, where you work, who your friends are, and when you’re away from home on vacation are pretty vulnerable and could be used by hackers to thoroughly exploit you.
Here are five simple tips that you can use to effectively put social media hackers at bay.
- Use Strong Passwords

Memorizing a password considered “strong” is no child’s play. Not even Mark Zuckerberg could fight the urge to create weak passwords for his accounts, at least until he was hacked on Twitter, Instagram and Pinterest – his password was later revealed to be “Dadada”.
While that may have come as a brutal lesson for the billionaire, it went to show just how many people out there want to be secure online but do not appreciate strong passwords. Your social media probably won’t attract as much interest from hackers as the founder of Facebook, but a successful attempt could be just as damaging.
You can use tools such as How Secure is My Account to rate your password and change it if necessary. Experts at Security Gladiators recommend that you also avoid using the same login credentials in more than one account to reduce the damage in case one of them is hacked. Password managers may be of assistance if you can’t create or memorize unique passwords.
- Be Choosy with Third Party Applications
Third party applications for popular social networking websites such as Facebook require your login details to access your account. Unless you’re sure about the legitimacy of the application, it is always advisable that you refrain from keying in your details until you verify that the app is from the company and is not a third-party replica.
Also, keep in mind that even if the application looks just like the genuine version, it could be a replica used by hackers to obtain login information and even work through the social media platform’s API. For this reason, downloading all your apps from Play Store and App Store for your Android device and iPhone respectively, or from the developer’s website are the only sure ways to ensure the app you’re installing is genuine.
- Review Your Privacy Settings
It’s wise to make a habit of reviewing your account’s privacy settings noting that social networking sites tend to regularly make changes to their terms and conditions. Once in a while, go through each of the accounts’ privacy settings and options and ensure that you’re aware and comfortable with what you share with the public. It is recommended that you make sensitive data private, as public information can be viewed by anyone online, including non-friends. A publically shared picture can be copied and used elsewhere without your consent or knowledge, leaving you vulnerable to identity theft, catfishing, and other scams. Also, take the time to review your approved list to see who can view your posted information and ensure you personally know them.
- Do Not Download
Most scams begin with a short email that has been made to look authentic with a shortened link and/or an innocent attachment. The link could be leading you to a scamming website while the attachment could be a data and password stealing application that could give someone permission to remotely control your social media account without your knowledge. Worse still, it could be a virus, which could distort your data and completely damage your device itself.
The best thing to do when you receive an email from an unfamiliar address is to review the sender’s email ID before clicking on any links or downloading any attachments. But what exactly on those email addresses should you be looking at?
Well, the suffix, according to Security Gladiators, is of great importance. No serious organization or authentic website would use a Yahoo, Outlook or Google account to send a business email. Also, look out for deliberate spelling mistakes in emails meant to imitate genuine ones – a single letter or number in the middle a 10-character address could be the difference between a phisher and a genuine sender.
- Enable Two-Factor Authentication
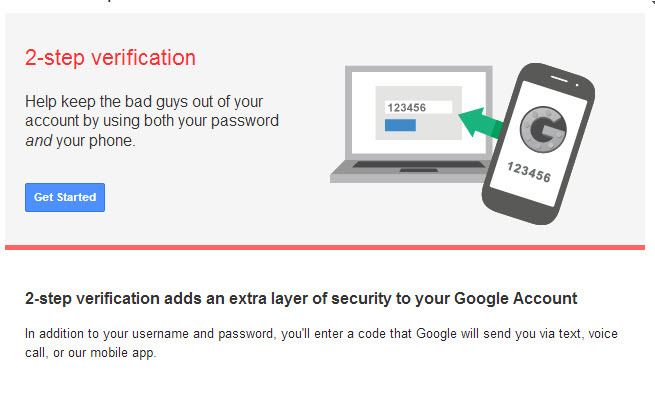
Two-factor authentication confirms your identity by utilizing an extra login requisite in addition to your password – usually a confirmation code sent to your phone or email whenever you try to log into your account. You may have heard of cases where hackers managed to get past Google’s 2FA, but that should not disrepute the technique as access to your account still depends entirely on your response to the hacking attempt. What happens is that the cybercriminal first obtains your password then slyly attempts to obtain the verification code from you in one form or another.
According to Alex MacCaw of Clearbit, who claims to have been targeted this way before, the attacker will send you a text message to the same phone number you receive your authentication code at, asking you to reply to their email with the code that will be sent to you shortly. What follows is their attempt to log in. If you got duped by their initial email, you will fall deeper into their trap when an actual verification code is sent to you just moments later. You would find it wise to obey the fake alert and, well, effectively compromise your own account.
When you think about, this is a calculated move that most anyone could be taken in by. It is where your keenness on checking email legitimacy comes in. As we have already pointed out, review the sender’s ID for spelling mistakes and questionable suffixes before reacting to thesesuspicious emails.
Social media may not be the first place a hacker would think of when they want to access your financial information, but it is when personal information is what they want. The above tips can help you stay completely out of reach of hackers and keep your interactions on the online platforms safe, private, and interesting.





![The Evolution of Twitter [Infographic]](https://lerablog.org/wp-content/plugins/wp-thumbie/timthumb.php?src=http://lerablog.org/wp-content/uploads/2015/03/The-Evolution-of-Twitter.jpg&w=300&h=140&zc=1)